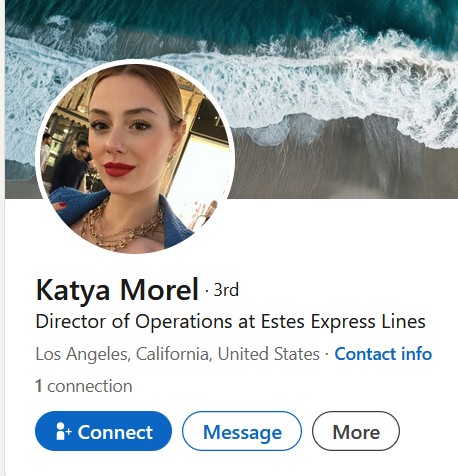
AUSTIN–If you’re a red-blooded male who just got hired at LTL carrier Estes Express, and on your first day you go looking to find the company’s beautiful Director of Operations whose picture you saw on LinkedIn, here’s a news flash: she doesn’t work there.
Not only that, she doesn’t exist, at least not by the name under that LinkedIn profile you saw.
That example was just one of several that came from the speakers at the National Motor Freight Traffic Association (NMFTA) cybersecurity conference here. The NMFTA is a nonprofit known for the classification system used by LTL carriers but increasingly as a leader in the battle against cyber crime threatening the nation’s supply chain.
The overwhelming message from speakers at the conference was that no matter how rapidly companies are building up their cybersecurity defenses, the bad guys are finding new ways, low-tech and high-tech, to get around them.
Low-tech vs. high-tech cyberattacks
And why would a picture of a comely woman in a non-existent job be a tool of cyber crooks? The answer falls clearly on the low-tech side of the divide.
While it was Todd Florence, the CIO of LTL carrier Estes Express Lines who told the audience about the fake director of operations, it was Ahmed Shah, senior security analyst at Malleum Information Security who, in a separate presentation, discussed how LInkedIn could have a role for cyber crooks.
Shah said the MGM cyber attack in 2023 utilized LinkedIn as an entrance to the company. “An attacker just went through LinkedIn, found a staff member, made a call and pretended they were that person,” Shah said. The fake MGM staff member, according to Shah, said he needed a reset in his password and multi factor authentication (MFA). “That was a 10-minute conversation, and you know the outcome of what happened,” Shah said of the attack on MGM.
Shah and other speakers repeatedly mentioned the specter of non-employees gaining access to a company through deception or even by something as basic as relying on the good graces of an employee who holds the door open at an office without checking their security credentials, allowing an intruder access.
But it was the story of the beautiful women on LinkedIn that, for obvious reasons, stuck out.
And while it might be memorable, Florence said it points to a bigger problem.
“It’s the social engineering that’s going on, and that’s largely what they’re using it for,” Florence said. If an Estes employee is lulled by the ability to connect with a striking-looking woman described as a colleague, the connection then opens the door for a cyber crook to “map out the organization,” Florence said. “They can call the service desk and be like, oh, I’m connected to this person.”
No love for LinkedIn
It was notable that LinkedIn came in for criticism in two separate presentations, that of Shah and Florence. The latter said “fighting it is difficult because LInkedIn has been historically difficult to deal with in this space,” noting that it isn’t just connections that are a problem. There are other aspects to the LinkedIn technology that cause problems for cybersecurity teams.
While cybersecurity attacks that shut down systems make the headlines–Florence went through a well-publicized one with Estes, and Forward Air (NASDAQ: FWRD) as a public company, also was up front about its own–a constant theme throughout the meeting is that just about everyone is getting bombarded with potential attacks day in and day out.
Thomas said that given the threats that never end–the phrase “we have to be right all the time, the crooks only have to be right once” was heard frequently–drivers can become a soft spot in Werner’s security. That’s why the vigilance needs to be constant. “If those alerts start to pop up, we can start to contact those drivers and find out whether they bought a new device and did they get that into the system,” Thomas said.
And time is absolutely of the essence.
An example of that was described by Florence, who said Estes recently had thwarted a cyberattack known in the business as “SVG.”
It starts with an employee on a system clicking on an email attachment that launches the executable program. “People are my worst enemies,” Florence said. “They click on everything because they’re terrified that if they don’t they will lose some business.”
Beating a 15-minute clock
The problem is the attachment that launches the attack will then start wreaking havoc, Florence said. But Estes, like other companies, has systems that immediately identified that an attack was under way, according to Florence. His team was able to shut down the attack in nine minutes.
And here’s the scary part: that only gave him six minutes to spare. Other victims lost control of their network within 15 minutes, Florence said.”We caught it and we shut it down,” he added.
Tom Baughman, executive vice president of technology at tank carrier Kenan Advantage Group, added to the case that drivers need to know they are a potential entry point for cybersecurity schemes.
“We have visual signage at all the terminals,” he said. Many of Kenan’s drivers return to their terminal each night, “so we get that touch point with them.”
But the cab is also a place for cybersecurity education, Baughman said. “We have training in the cabs, pushing out little videos,” he said. A goal with that approach, he added, is to “teach the why”: why are cyber crooks doing what they’re doing?
Driver acceptance of the message has been positive, according to Baughman. “They care about the company and not paralyzing the business,” he said.
The panel of the three carriers was not only focused on low-tech issues; AI inevitably entered the discussion.
Florence said when Microsoft and other software providers release various software updates weekly, a day informally known as Patch Tuesday, “the threat actors have leveraged their AI engines to excavate those patches and are firing shotgun tracks across the internet.You’ll see chunks of the same type of attack the next day.”
But the use of AI by cyber crooks can be more publicly visible than where it’s driving the bombardment of a target’s systems. Thomas said a fake AI-generated video of Werner CEO Derek Leathers, making “statements” that were problematic, was part of a “sophisticated” phishing campaign. Werner tried to replicate the video; the cost was a grand total of $30. “It was very realistic,” he said of the product.
How it impacts M&A
The issue of cybersecurity has become a major feature of merger & acquisition activity. Baughman said Kenan has done several acquisitions in recent years. “And so as we have gone through that, it’s a challenge because you don’t know what type of software they’re using up front,” he said. It’s a long checklist of processes needed to get the technology issues connected with an acquisition out of the way, he said.
But as Kenan has done more acquisitions, “I think we have a pretty good checklist now,” Baughman said. “We can go in and say, these are the three or four things that have to change immediately. These are the three or four things that have the ability to wait a little bit longer and then the movement of the systems is last.”
Florence said when Estes is looking at an acquisition, “I literally spend about five to 10 minutes on business stuff, and then it’s all cybersecurity, trying to understand where they’re weak or strong.”
Some smaller acquisition targets will have a managed service provider (MSP), an outside company that is essentially an outsourced tech team. But Florence said often when he speaks with that MFA, he will find that a longer list of cybersecurity tools offered by the provider will have been declined by the trucking company in a bid to cut costs.
And on the low-tech side, Thomas said the smaller acquisition targets can be particularly vulnerable to those physical intrusions that can be part of a cyberattack, like a weak surveillance camera system or easily opened doors.
More articles by John Kingston
DAT execs in two forums discuss how it seeks to reshape the freight sector
State of Freight takeaways: some signs are pointing higher
NMFTA’s freight classification overhaul: surprising shipper preparedness
The post Beautiful women, open doors and drivers: trucking cybersecurity risks proliferate appeared first on FreightWaves.